BL301.BIN Injection
Some Amlogic devices do have problems with wake-up from suspend/power off by IR remote, CEC or WOL, this is related to a poorly configured bootloader.
This is the reason for the new tool that we have created, inject_bl301!
This tool is written by Team CoreELEC and exclusive for Amlogic devices running CoreELEC!
What is the purpose of this tool:
If you own an Amlogic device that have issues with wake-up features like IR remote wake-up, CEC or WOL wake-up then you can use this tool to fix those issues.
Currently confirmed devices it does NOT work
- Magicsee N5 S905L
- TX3 S905X3 from Aliexpress
- X95 max S905X3
Please remember using the tool on one of these device may stop it from booting!
The device does then needed to be recovered by shorting out the eMMC while a uSD prepared by Amlogic Burncardmaker is needed!
GXL:
Warning! GXL support is still experimental!
It is possible that the injection brick your device and it will not boot anymore!
It will be needed to short out the eMMC to recover the Amlogic device.
So there is no warranty by team CoreELEC if the injection will be successful or not!
Please ensure to have the newest firmware used on the device. Minimum required is Android 7!
How it works:
inject_bl301 will exchange the bl301 blob of the bootloader and leave the rest untouched. This blob is responsible for handling the resume functions when in suspend/power off mode. By exchanging this blob the bootloader wake-up features can be fixed/enabled.
This has the advantage that CoreELEC can still use the original bootloader and it is almost impossible to brick the device as the bl301 bootloader blob only gets activated when sending the device to suspend/power off. If you encounter any problems then you can write your original bootloader backup to the device and the bootloader will be restored like it was before the injection.
Currently supported Amlogic SoC’s:
SoC ID: 0x21 - GXL (S805X, S805Y, S905X, S905D, S905W, S905L, S905M2)
SoC ID: 0x28 - G12A (S905X2)
SoC ID: 0x29 - G12B (S922X, A311D)
SoC ID: 0x2B - SM1 (S905X3, S905D3)
Hardkernel Odroid devices (N2(+), C4, HC4):
There is no need to run this injection on Hardkernel Odroid devices as the bootloader provided by CoreELEC already support these BL301 features.
How to use the inject_bl301 tool:
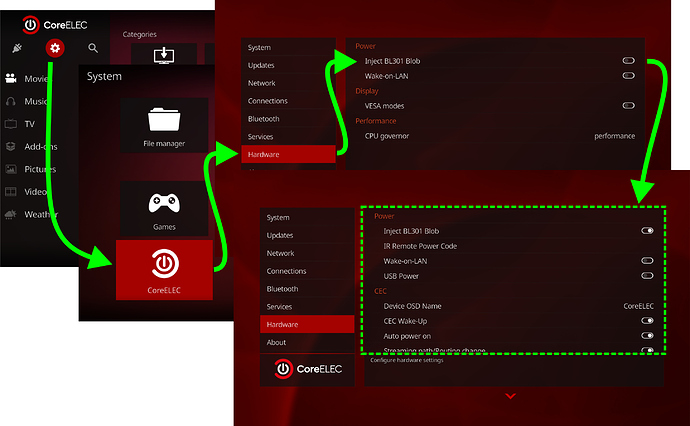
How to enable/disable:
Settings
CoreELEC
Hardware
Inject BL301 Blob
If the BL301 blob got injected some additional features device type dependent are coming available after a reboot. Any change of the hardware settings will require a reboot to become active.
Usage of the tool by command line:
Usage: inject_bl301 [options] [BL301.bin file...]
[options]
-b define local bootloader blob BL301.bin
-l define local bootloader binary dump
-d upload the debug output to http://ix.io
-s define a system root path (needed for update.sh)
-Y auto confirm user interaction request
-h print this help
Firstly you must SSH to your device and run the tool by entering:
inject_bl301
Push enter and the tool will print out some debug information like this:
CoreELEC:~ # inject_bl301
Starting bootloader blob BL301 injection tool...
This tool can be used to update the bootloader
blob BL301 of the vendor bootloader on the internal
eMMC. This bootloader blob BL301 is customized by
Team CoreELEC to support all wake-up features like
CEC, Wake-On-LAN, IR, and GPIO wake-up from
suspend or power off state!
Device serial number: 280b4000012e33000009313256474d50
Using CPU type G12A (28): S905D2, S905X2
Using binary type because of CoreELEC DT-ID: Generic
Using /dev/bootloader as bootloader partition
Testing bootloader for package version v2...
Did not find Amlogic image v2 header magic!
Searching TOC_HEADER. Please wait...
Found TOC_HEADER at: 0x00010210
Name: AA640001
Serial Number: 12345678
Flags: 0
TOC ENTRY #0
UUID: 9766FD3D89BEE849AE5D78A140608213
Offset Address: 0x5C000 (absolute: 0x6C210)
Size: 0xE570
Flags: 0x0
Found BL30 blob image at: 0x0006C210
Amlogic magic: @AML
Old signature: FCC1D8D71366E27A3950A195E53BFEDF66B87966D9272D4B0312558DE4BE0FD7
Using BL301.bin: Generic_28_29_bl301.bin
Use config.ini value: usbpower = 0x01
Use config.ini value: remotewakeup = 0xeb14ff00
Use config.ini value: cec_osd_name = NEO T5
New signature: F227E1C7D9B03417A8AF7D3C2DD96C412B362FB974FD4C6A1E65F12EBFC601F7
Please confirm to write the bootloader blob BL301 to
the internal eMMC! Please ensure to update first the device
to the last vendor firmware! And remember if the vendor
firmware get updated you have to do this step again as the
bootloader blob will be overwritten!
Continue? [y/n] y
Answer the question with 'y' to inject the CoreELEC bl301 binary to the Amlogic device.
Then the inject_bl301 tool will continue and make a backup of the original vendor bootloader before injecting the CoreELEC blob:
Make backup of vendor bootloader to: /flash/280b4000012e33000009313256474d50_bl301.bin
Finished update of BL301.bin on internal eMMC!
Please reboot device now and enjoy the new CoreELEC wake-up features!
Now the injection of the bl301 blob to the Amlogic device is finished and you just need to reboot the device by typing:
sync && reboot
After your device has rebooted you can start to customize our config.ini like described here:
How to configure IR wakeup code
The config.ini key values are read by the tool inject_bl301 on every boot into CoreELEC. If any value got changed the blob get injected again with the updated values.
Was the injection successful?
Just run the tool again and if the old signature and the new signature matches then the bl301 bootloader blob got updated successfully. It will not cause any problems if you run the tool multiple times:
CoreELEC:~ # inject_bl301
Starting bootloader blob BL301 injection tool...
This tool can be used to update the bootloader
blob BL301 of the vendor bootloader on the internal
eMMC. This bootloader blob BL301 is customized by
Team CoreELEC to support all wake-up features like
CEC, Wake-On-LAN, IR, and GPIO wake-up from
suspend or power off state!
Device serial number: 280b4000012e33000009313256474d50
Using CPU type G12A (28): S905D2, S905X2
Using binary type because of CoreELEC DT-ID: Generic
Using /dev/bootloader as bootloader partition
Testing bootloader for package version v2...
Did not find Amlogic image v2 header magic!
Searching TOC_HEADER. Please wait...
Found TOC_HEADER at: 0x00010210
Name: AA640001
Serial Number: 12345678
Flags: 0
TOC ENTRY #0
UUID: 9766FD3D89BEE849AE5D78A140608213
Offset Address: 0x5C000 (absolute: 0x6C210)
Size: 0xE570
Flags: 0x0
Found BL30 blob image at: 0x0006C210
Amlogic magic: @AML
Old signature: F227E1C7D9B03417A8AF7D3C2DD96C412B362FB974FD4C6A1E65F12EBFC601F7
Using BL301.bin: Generic_28_29_bl301.bin
Use config.ini value: usbpower = 0x01
Use config.ini value: remotewakeup = 0xeb14ff00
Use config.ini value: cec_osd_name = NEO T5
New signature: F227E1C7D9B03417A8AF7D3C2DD96C412B362FB974FD4C6A1E65F12EBFC601F7
Update of BL301.bin on eMMC is not needed, exit now...
Restore the vendor bootloader:
There are two options to restore the vendor bootloader.
-
The tool is making a backup of the vendor bootloader before the first injection to the internal eMMC. The backup can be found on your CoreELEC media at:
/flash/<CPU_SERIAL>_bl301.binFirstly you must SSH to your device and run the
ddcommand:dd if=/flash/<CPU_SERIAL>_bl301.bin of=/dev/bootloader conv=fsync bs=512 sync && rebootAfter the reboot the bootloader is restored like no injection was happening at all.
-
Use the typical Amlogic recovery method like with Burncardmaker or the USB burning tool to restore the vendor bootloader. When restoring by a vendor image the bootloader get restored too. Please keep in mind to
Reminder:
The injection is NOT applied automatic and so every time you restore your Amlogic device with a vendor firmware image then you will have to run the tool again as the bootloader will be overwritten and restored as well.
If the bl301 bootloader blob was injected once it get updated automatically when updating the CoreELEC system by the common update method and on every boot into CoreELEC.
Problems, Questions:
Please use this thread to ask for help: Bl301 injection, problems, help,