As your last resort put this in /storage/.config/autostart.sh to delete file automatically.
(
while [ ! -f /storage/inject_bl301.log ]; do sleep 2; done
sleep 3
rm -f /storage/inject_bl301.log
)&As your last resort put this in /storage/.config/autostart.sh to delete file automatically.
(
while [ ! -f /storage/inject_bl301.log ]; do sleep 2; done
sleep 3
rm -f /storage/inject_bl301.log
)&This whole issue is confusing to me and doesn’t make sense. I’m not going to worry about since it doesn’t seem to cause any functional impact for me.
Though I would like to be able to shut off all the functionality including the inject BL301 service. Like I said I’ve been setting my options all along in config.ini and it’s no problem to continue doing that. Since my device does not support the blob there doesn’t seem to be any sense in it running or even starting up and leaving a log to say it can’t run. But I don’t know what’s involved in these things so I’m not one to say.
At the least can I put in a request to have the location of the log fixed? It should go to /storage/logfiles not /storage.
Yes I did think about running a script to kill the log. I’ll just do that if it comes down to it. Thanks for the example script.
Your bootloader looks encrypted, injection is not possible.
You can dump the bootloader and I can take a look if really encrypted. Run this command and upload the resulting img:
dd if=/dev/bootloader of=/storage/backup/bootloader.img
you can’t answer early!
I have a limit of 3 posts
HERE IS THE FILE: WeTransfer - Send Large Files & Share Photos Online - Up to 2GB Free
You need ti upload this file somewhere or attach it to a post.
HERE IS THE FILE: https://we.tl/t-RUWfUwLx2u
Thank you, I can confirm your bootloader is encrypted. Injection is not possible!
This is paradoxal. A tool developed for Odroid N2 basically, it works on all kinds of other platforms, and it doesn’t on my N2. I want to smash my head.
Fresh install of CE 9.2.2, dual booting on a emmc.Having all kinds of failures in attempt to boot the N2 with GPIO and remote, and when I run the command in SSH this is the result:
login as: root
root@192.168.1.226’s password:
##############################################
# CoreELEC #
# https://coreelec.org #
##############################################
CoreELEC (official): 9.2.2 (Amlogic-ng.arm)
CoreELEC:~ # inject_bl301
Starting bootloader blob BL301 injection tool...
This tool can be used to update the bootloader
blob BL301 of the vendor bootloader on the internal
eMMC. This bootloader blob BL301 is customized by
Team CoreELEC to support all wake-up features like
CEC, Wake-On-LAN, IR, and GPIO wake-up from
suspend or power off state!
Device serial number: 290a400001081e000003383448564d50
Using CPU type G12B (29): S922X, A311D
System is not supported by BL301.bin injection: g12b_s922x_odroid_n2
CoreELEC:~ #
Trying to launch by GUI is not available. Only things I see in 9.2.2 are these,
On N2 bl301 is already hardcoded into the bootloader.
Do you have the boot switch on the N2 in eMMC position?
Hey , I dont mind powering shutting down via within kodi but only way to turn back on is pull power lead out and back into box, original android box remote, power button doesnt work or respond at all with coreelec.
Any remotes that work and to turn it on ?
You should start telling which device you are using.
Apologies forgot, X10 Max 8K S905x3 Android 9 TV Box, came with a generic basic crappy remote which works only within android. Just been usin a mouse within coreelec kodi.
If you find out the gpio for the power button it can be also activated.
Just came across that but get this when tried to enable it
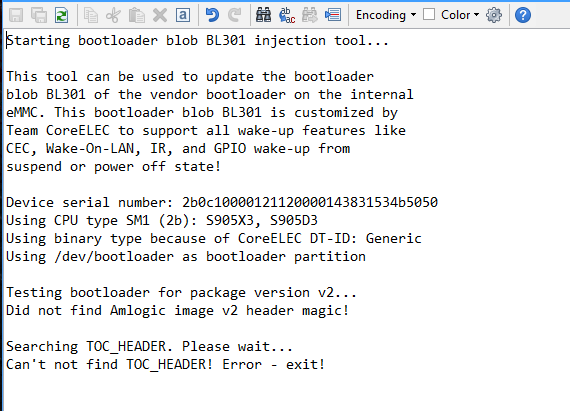
Then the bootloader is encrypted and you can’t do anything.
wow really, why would it be encrypted on such a device , is there way I can at least put it into sleep mode if not using it ?
no, contact your vendor if he will probably fix the bootloader.
you mean the seller of box, how could they fix the bootloader ?
About | FAQ | Terms of Service | Privacy Policy | Legal Notice